The 6 Elements of An Effective Phishing Awareness Training Program

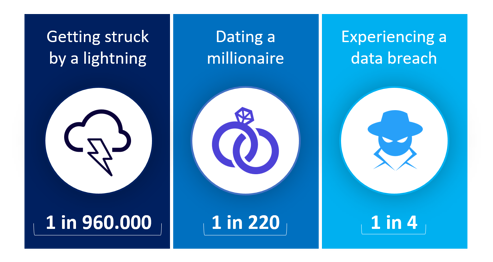
Effective phishing awareness programs have proven to reduce risk by up to 80% within six months, emphasising the point that you cannot depend on technical defences alone. However, successful ones don’t happen by accident, here is what they need to include:
1. Deliver the Right Content in the Right Way to the Right Users
Long classroom sessions where users are not engaged will not get the job done.
Content needs to be delivered in digestible chunks so that the User can absorb it.
User attention spans are getting shorter as the pressure of work and deadlines increases so content that is delivered in modules of less than 8 to 10 minutes have been shown to be much more effective because they do not have inordinate impact on productivity.